A long-running debate between Mac owners and those folks who use other platforms is whether or not malware exists for macOS. It does! Mac owners tend to be very defensive (and, sadly, sometimes offensive) about macOS, because of years of slights when Windows was in the ascendance and virus ridden.
A long-running debate between Mac owners and those folks who use other platforms is whether or not malware exists for macOS. It does! Mac owners tend to be very defensive (and, sadly, sometimes offensive) about macOS, because of years of slights when Windows was in the ascendance and virus ridden.
These days, most malware that attacks computers and mobile systems in the wild comes from visiting a website, receiving and opening an attachment via email or a text message, or following a link in an email that misleads you into thinking you’re at a legitimate site, into which you mistakenly enter legitimate credentials.
And most of that malware is old. On the desktop, most attacks focus on older versions of Windows, some using variants of malware that are several years old, according to a recent update from the analysis firm Check Point. On the mobile side, 60 percent of attacks come a single 15-month old attack called Hummingbad, which is often delivered as a Trojan horse—malware hidden inside what appears to be a legitimate app.
Apple has managed to avoid attacks that first appear in the wild, usually nipping them in the bud either through advance disclosure from security researchers or the sheer difficulty of exploiting a flaw that’s revealed before a patch is available. It’s also never had a long-running exploit that was known to exist, wasn’t fully patched in old releases, and had a large number of users still running those old releases.
This makes Apple’s OSes seem more invulnerable than they are. But is an anti-virus package the answer? In my view, and that of many security experts, including those who have found vulnerabilities in macOS and iOS, no—in most cases, and I’ll describe those that make sense later. Macworld hasn’t reviewed anti-virus software for years, which may indicate the larger editorial philosophy as well.
The biggest risk to Mac users is the rising tide of a specific kind of malware, called ransomware, which you can defend against using targeted anti-malware software that doesn’t rely on virus definitions.
Ransomware leading threat
We often talk about malware by the vector by which it spreads—how does it insinuate itself into your computer? Malware can distribute itself in several different ways. You may see it…:
- As a malicious attachment, like a virus that runs when you open the file.
- As a Trojan horse, explained above.
- Through phishing, or email or a text message that fools you into clicking a link that subverts your system
- Via spear-phishing, which uses targeted information about a victim to appear more genuine and likely to be clicked or acted on
- Through a remote network attack, popular right now with poorly secured Internet of Things (IoT) devices. (For IoT, that means most of them, unfortunately.)
These vectors all exist for macOS, but the best recent path for infection has been through a Trojan horse. That’s partly because it’s easier to convince someone to install software they think is legitimate than to find another path of exploit. We saw this for Macs in 2016 with malware inserted into the BitTorrent client Transmission, and in February 2017 when a different kind of macOS malware appeared.
Both of those Trojan horses were ransomware, which isn’t a new vector of infection. Rather, it can spread through any of the vectors noted above. But it’s proven a vicious problem under Windows and some other desktop OSes, because unlike most previous malware, it affects files only found in “userspace”: that is, our documents and settings.
Ransomware uses an encryption key to scramble the contents of all of our user data, and puts an executable wrapper around it, so that when you try to open a file, it runs and tells you how to pay a ransom in Bitcoin to obtain the decryption key. The price for individuals is often relatively modest and you can sometimes negotiate a lower payment. Without the key, your files on the drive are lost forever unless you have a backup or archive prior to the encryption. (Time Machine and other backups will dutifully copy the encrypted version, so you have to discover the problem before your oldest good copies have been overwritten.)
Because ransomware doesn’t need that high a level of permission to run, it’s relatively easy to spread it. In mid-2016, researchers found JavaScript-only Windows ransomware that even runs outside a browser. Because it’s inexpensive to make or modify, a lot of people apparently distribute it. Check Point estimates that 10 percent of infections in the second half of 2016 across all systems were ransomware variants, and the number keeps climbing. Attackers have many families of ransomware code to choose from, and it’s easy to customize it.
I assume there will be multiple successful ransomware attacks against Mac users, though likely shut down quickly by Apple through its Xprotect system, which automatically updates with known malware signatures as they become available. However, before these attacks hit you, you can protect yourself.
Tools against broad categories of popular attack
You can protect yourself against ransomware and network attacks, as well as some categories of Trojan horse that aren’t ransomware in nature, by installing a few affordable and inexpensive tools.
Ransomware’s harm led Jonathan Zdziarski to create Little Flocker ($20 for personal use, up to 5 computers), a macOS tool for detecting and either blocking or permitting access by apps to specific folders. I’ve been using Little Flocker for months, and Zdziarski made a continuous series of improvements that reduces the amount of training required as you update software to new versions. Once ransomware gets its teeth in, it relies almost entirely on not being watched, and Little Flocker keeps its eyes peeled. It also monitors for apps that capture keystrokes and use mics and cameras. (Zdziarski recently joined Apple, and the future of Little Flocker isn’t certain, but it’s so useful that I hope it finds a new home.)
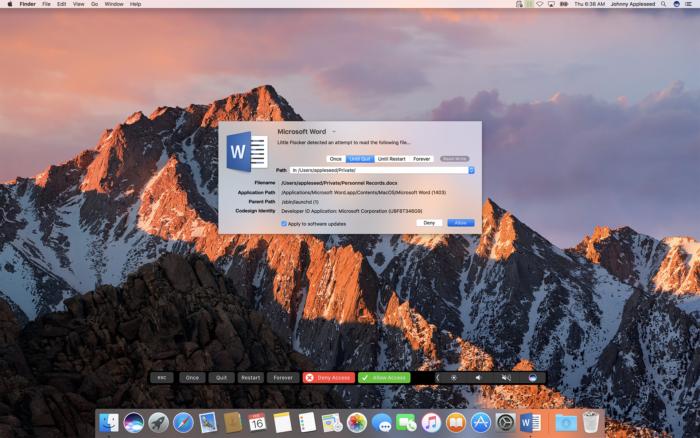
Little Flocker
Paired with Little Flocker is Block Block, free and still in beta, which monitors for software trying to install files that allow it to launch automatically after a restart or when killed. That can help with adware and other unwanted software, too.
Should a macOS ransomware package find effective distribution, Little Flocker plus Block Block should prevent and alert you to something bad happening, at which point you can check in with Macworld and use social networking to find out what’s happening—or be the first to report an outbreak.
A parallel and effective way to block malicious software from calling home and sharing your information is a firewall and network monitor. We like Little Snitch, a mature app that examines everything coming in and leaving your Mac, and uses rules to permit authorized behavior but alert you to everything else. Malware tries to talk back to centralized servers, and while there are tricks to work around firewalls, an app that isn’t supposed to have a network connection that suddenly tries to summon the Internet gets noticed. (We last reviewed Little Snitch in 2015 for the first release of its current version.)
Rich Mogull, head of security analysis firm Securosis who has a deep expertise in Apple-related issues, says that he doesn’t use anti-virus software at all. He relies on Little Snitch, Little Flocker, and Block Block for network, input, and file monitoring, and expects his email hosting companies to staff the viral barricades.
But what about the really bad stuff?
You might think the kind of things I’m mentioning above seem very penny ante. If you read Apple’s security updates that list of often dozens of security holes patched in every OS release and in built-in software, you might think there’s a churning morass of flaws that could reach out and grab you via Safari or your inbox.
And that’s partly true. A lot of vicious malware for macOS and iOS does exist. It’s just that it’s too valuable to use against the likes of you and me. The good stuff sells for $100,000s or millions of dollars in gray and black markets, and get used by firms that sell their services to governments, by criminal syndicates, and other murky parties.
Those exploits are held close to the vest, rather than pushed into the wild, because of that easily obtain value in existing markets. When they’re used, it’s sparingly, and often against prime targets. For instance, last summer, a human-right activist in the United Arab Emirates, Ahmed Mansoor, had three separate zero-day (previously unknown) exploits attempted against him.
These were for iOS, which doesn’t allow anti-virus software the kind of permission it needs to run, but similar weaknesses were also found in macOS. Because these were unknown and subtle, no Mac anti-virus software would have detected and blocked them. Apple immediately patched the flaws in iOS and then shortly after in macOS, rendering them useless.
It’s not that no risk from a more general category of malware exists for Mac users. Rather, the highest likelihood is that your files will be locked away, and, thankfully, it’s also the easiest attack you can protect yourself against.
Given that Zdziarski has joined Apple, following in the footsteps in the last year or so of some other prominent researchers, we might hope that these kinds of tools find themselves neatly and seamlessly into future versions of macOS.