Imagine somebody walking to a checking counter at an airport, and using his boarding pass to hack a nearby computer. That isn’t a plot taken from sci-fi movies, it’s something that can be in news in the coming days. A researcher has demonstrated a method of creating malicious barcode strings that could allow an attacker to trigger shell commands. The vulnerability affects almost every barcode sensor currently in use, Gadgets 360 was told.
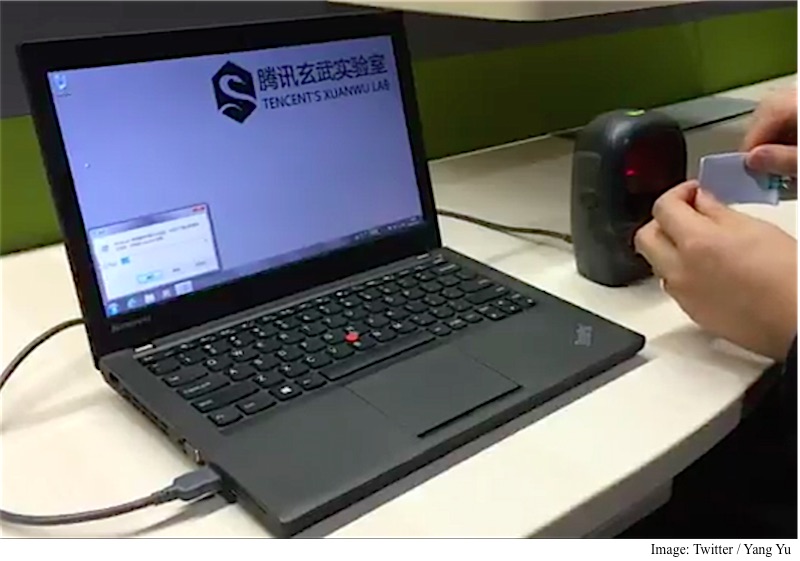
At the MobilePwn2Own, PacSec 2015 conference in Tokyo, Yang Yu, founder and head of Tencent’s Xuanwu Lab, demonstrated a vulnerability that he referred to as “BadBarcode,” which allows an attacker to use a piece of paper to gain access to a computer.
In a detailed presentation, which is available on SlideShare, Yu has revealed a vulnerability in the way barcode sensors are fundamentally designed.
Most of the barcode in use today, including the ones that you see on postal packages and behind retail boxes and containers, utilise the Code 128 standard or its derivative – and support ASCII characters. Barcode scanners, furthermore, work as a keyboard emulation device.
As you can see in the image below, the ASCII protocol includes characters for system’s combinations keys (e.g. Ctrl). An attacker could use these combinations and open a shell and type commands.
Yu further explained that because most barcode scanners use Advanced Data Formatting (ADF), scanned data can be manipulated by an attacker before the data is transmitted to host device. Moving along, a specified key can also be sent to a computer, for this reason even barcode scanners that don’t have a touch interface are vulnerable, Yu writes.
“According to our research, almost all of the keyboard wedge barcode scanners are affected to varying degrees. So, we think this is a big threat,” Yu told Gadgets 360 in an emailed statement Tuesday. “BadBarcode is not a vulnerability of a certain product. We even may not make it clear that BadBarcode is the problem of scanners or host systems.”
“It affects the entire barcode scanner-related industries. That is why we hope that manufacturers will see our research. In fact, we are pleased to know, there are some manufacturers have begun to consider to solve this problem after they knew BadBarcode.”
Yu noted that BadBarcode is a serious problem. “Host system using keyboard emulation barcode scanner is potentially vulnerable. Kiosks with touch screen and barcode scanner are easy to be compromised. Barcode scanner that support ADF or some special keyboard emulation features can be utilised to achieve automatic and advanced attack. Other device via keyboard emulation connection might suffer from the same problem,” he wrote.
At the same event, a researcher had discovered a vulnerability in Chrome for Android that gives anattacker access to the handset. Also, researchers had found vulnerabilities in Samsung’s smartphones that allows an attacker to intercept calls and messages by making the handsets connect to a compromised base station.